Social Media Hacking: How to Protect Your Account

Table of contents
There’s no denying that social media has become an important part of a B2B marketing strategy. No other channel goes further in creating real relationships with your customers, and a community around your brand.
However, no business can reap the benefits of social media if it’s not able to protect its accounts from hackers. Scammers, impersonators, and hackers are becoming an ever-growing threat to businesses on social media platforms and can wreak havoc.
In this article, we’ll discuss the most common social media security risks, along with best practices to protect your social media accounts from hackers. It’ll help you stay ahead of potential attacks and offer your B2B services that your customers can trust.
Quick Links:
- 6 Common Social Media Security Risks
- 9 Best Practices to Protect Social Media Accounts from Hackers
- What to Do if Your Social Accounts Are Compromised
6 Common Social Media Security Risks
Here’s a list of the most common social media security risks that you need to know.
1. Human/Employee Error
According to recent stats, 82% of cybersecurity breaches, including misuse, errors, and social attacks, involve human error.
While it’s useful to have several employees with access to your brand’s social accounts for a variety of reasons, this also increases the risk of human error.
Sometimes downloading the wrong file or clicking on the wrong link can cause social media security issues. There are a few ways to mitigate the potential human error:
- Use a social media management platform with unique logins and permissions to prevent too much access to administrator privileges.
- If you’re not using a social media management platform, use a password safe to ensure that passwords stay secure.
- Educate employees about potential fishing attacks, and enable two-factor authentication across the board.
We’ll go over more ways to secure your social profiles and make sure they’re impervious to cyberattacks.
2. Unattended Social Media Accounts
Brands, especially B2B businesses, need to manage multiple social media accounts on different channels. It allows them to maintain a consistent online presence across different platforms to reach more potential clients.
But you must never leave the accounts that you don’t use anymore unattended, as they make for an easy target for hackers.
Once hackers gain control of such accounts, they can use them to start sharing fraudulent posts and messages using your brand’s name. It can badly damage your brand’s reputation and you could permanently lose access to that account.
3. Phishing Attacks
The goal of a phishing attack is to extract the username and password of your social media account using a fake link, containing malware. It’s one of the most common types of social media attacks and it helps hackers to take control of your accounts.
4. Imposter Accounts
It’s easy for a hacker to create an account on social media that looks like it belongs to your brand. Hackers can use such accounts to share misleading and incorrect information about your business to damage your brand’s reputation.
Additionally, they can also start interacting with your customers and attempt to extract their personal information, including usernames, passwords, and bank card details on your behalf. You won’t be able to detect such accounts unless your customers reach out to you.
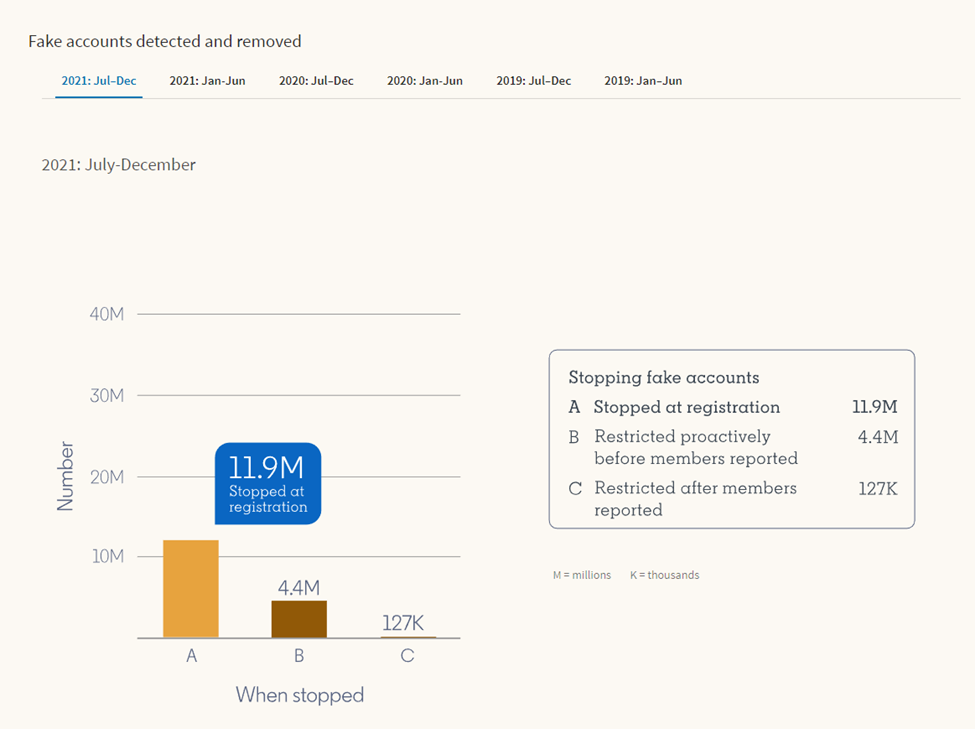
The latest transparency report of LinkedIn shows that they blocked 11.9 million fake accounts at the registration step in just six months. In addition, 4.4 million fake accounts were deleted after they got registered, but before members reported them,
However, there were still 127,000 fake accounts that the platform blocked after the members reported them.
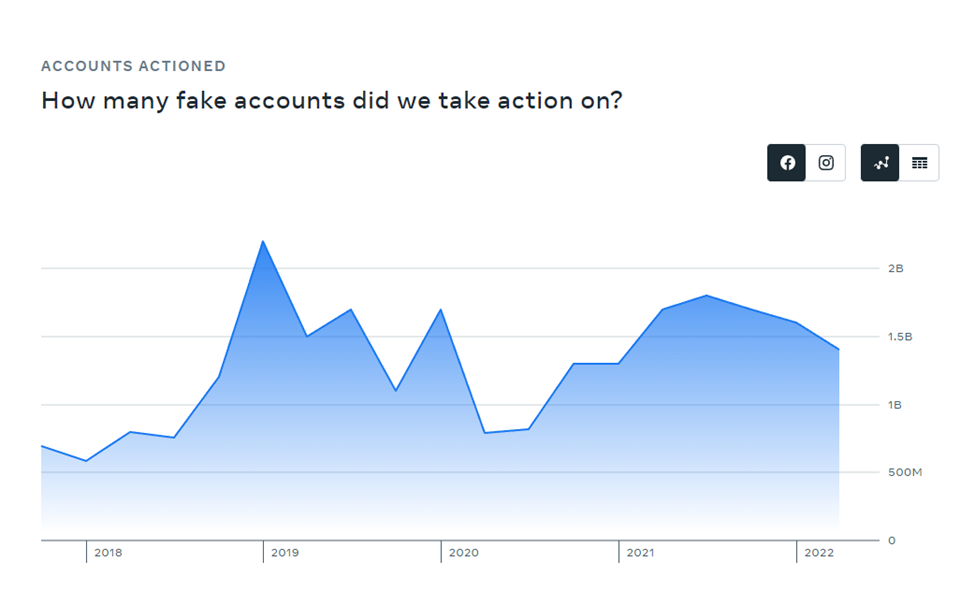
In addition, Facebook reports that it blocked 1.4 billion fake accounts in Q2 2022.
5. Ad Scams
Ad scams are becoming a growing problem on social media platforms, especially Facebook and Instagram. Hackers and scammers create fake ads using identifying information, such as logos and slogans, from real brands to make the ads look real. These ads can lead to reputational damage for your company.
6. Vulnerable Third-Party Apps
Using a multi-layer approach to ensure security and customer data protection, such as using two-factor authentication, is great. However, these layers won’t be enough if you have linked your account to a vulnerable third-party app.
Linking your account to an app means sharing your credentials with them, and a cybercriminal can gain access to your account by hacking such an app.
Hackers used the same approach and accessed Twitter accounts that were linked to the International Olympics Committee. They used a third-party analytics app, and one of the victims of this incident was FC Barcelona.
9 Best Practices to Protect Social Media Accounts from Hackers
The following are the best practices that business owners can use to protect their social media accounts from hackers.
1. Secure Your Login Information
Weak passwords are often the biggest security risk and they’re also the easiest to fix. While you can make 209 billion different combinations with eight lowercase letters, such a password can be cracked instantly.
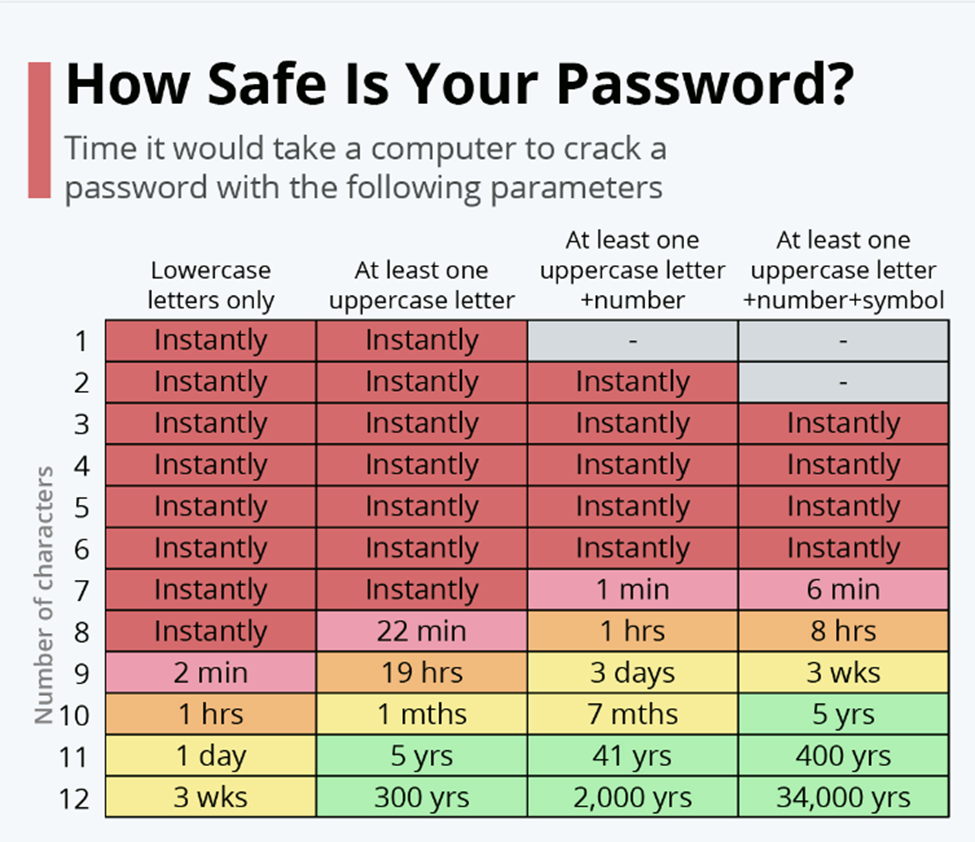
Therefore, you must create a strong password for your social media accounts. Here’s a list of techniques that you can use to create a password that’ll be nearly impossible to crack.
- It must be at least 12 characters long
- It should contain random combinations of lower and uppercase punctuations, symbols, numbers, and letters.
- It mustn’t have any relation to your business, such as zip code, location, name, etc.
Example of a strong password: 7%tVI6e$Y5ut
Other than creating a strong password, it’s also important to make sure that you don’t use the same password for multiple accounts. Plus, make a habit of changing all your passwords after three months. This way, the hacker won’t be able to access your other accounts if one of them is hacked.
2. Limit Access to Accounts
It’s important to determine what your employees can see and do while using your brand’s social media account. From read-only to admin mode, you should create custom roles in order to protect your social media information.
For example, if you have employees who reach and communicate with the brands that can use your services, then you don’t want to provide them with admin mode access. They only need to use the messaging function of your social media platforms to reach your target audience.
Keep in mind that each person who can access your business accounts on social media, can be a security risk. It’ll increase the risk of human error, which will provide hackers with the opportunity to steal your sensitive information.
Make sure that you manage your teams based on their roles by defining different groups so that they can access only those functions of your social media accounts they need to perform their jobs. It’ll allow for a more targeted approach and make it easy for you to monitor the performance of your team.
3. Use Social Media Governance to Optimize Risk Management
Providing your employees with clear guidelines on how to use your social media accounts can minimize the risk of a security breach. It’ll allow your employees to understand what risks social media poses to your brand and how to use your accounts safely.
Your social media policy should include guidelines for confidentiality, brand voice, communication, and copyrights. However, you must keep in mind that social media governance goes beyond having a social media policy.
It’s about educating your communication and marketing teams about safe and secure day-to-day practices that they must embed in their strategy to use your social media accounts. It’ll help mitigate the inherent risks that social media poses to your organization and optimize risk management.
You can create a social media policy, containing “Dos and Don’ts”, that will help your employees to learn how to avoid social media attacks.
4. Use a Secure or Private Wi-Fi Network
It’s advisable to use only a secure or private Wi-Fi network, especially when you’re using it to manage your brand’s social media accounts. You don’t want to use a public Wi-Fi network, as it increases the risk of being hacked.
Hackers can create a free Wi-Fi connection and make it available for you and your employees. Connecting to such a network can allow the hacker to see sensitive information about your social media accounts.
Plus, it’ll also allow the hacker to inject a virus or malware into the devices that you’re using to manage your data. It can also lead to a ransomware attack, which is one of the deadliest cyberattacks.
Therefore, you should always use a private and fully secure Wi-Fi connection to manage your social media accounts. You can also use encryption and VPN services to further improve your network security and protect the communication of your different teams.
It’ll allow you to protect your data transmission with the help of encryption technology. Not only will it secure communication between your teams but it’ll also ensure the protection of data being transmitted between your server and browser.
5. Never Log in Using Unknown Links
As mentioned, phishing is one of the most common types of strategies that hackers use to steal your usernames and passwords. According to statistics by APWG, more than 23% of phishing attacks take place on social media.
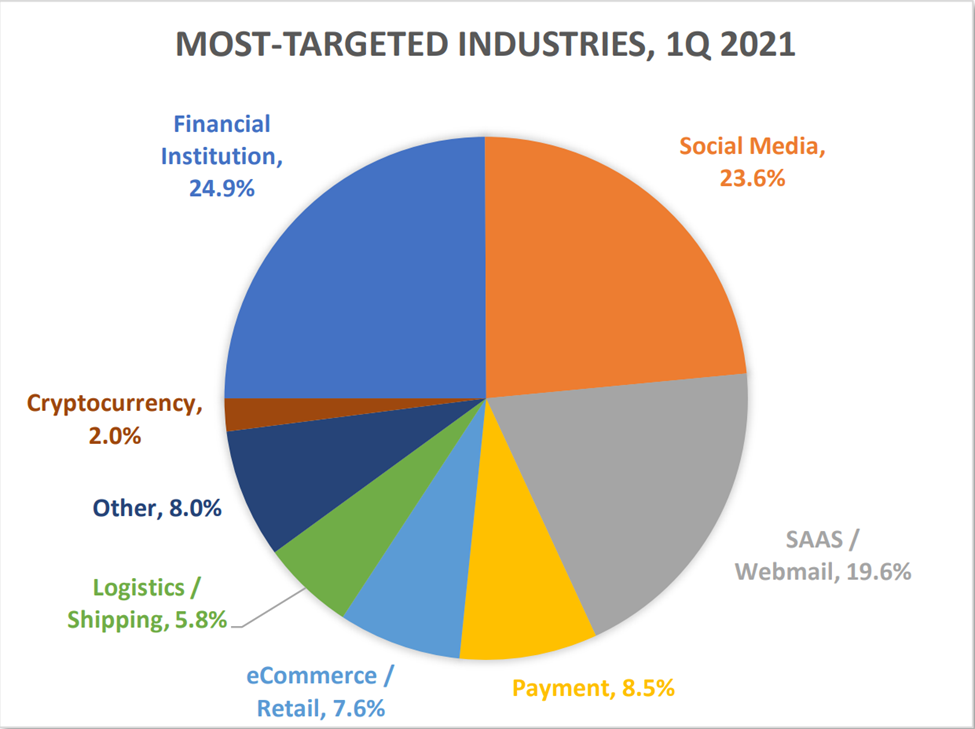
They send fake links to individual and business accounts that redirect them to another page, which looks like it’s authentic.
But once you put your credentials in, the information directly goes to the hacker, allowing them to gain access to your business accounts. So, if you see any links sent by unknown people to your social media accounts, do not open them.
You’ll also need to educate your employees about these hacking tactics so that they also refrain from clicking on such links. They can also lead to suspicious websites with viruses and malware that can gain access to your data or damage your devices.
Most phishing links come in the form of contests from a non-verified account, quizzes with trendy topics related to your business, and clickbait content and words.
6. Use Two-Factor Authentication
Enabling two-factor authentication, also known as 2FA, is another excellent way to protect your brand’s social media account. It’s about adding another security layer, an identifying step, to your account, like your password.
Usually, your account password is paired with a unique identifying code, generated in real-time. Even if the hacker gets access to your account password, they won’t be able to cross the second identifying step, which mitigates the risk of being hacked greatly.
7. Secure Your Business Hardware
Securing the hardware that your teams use to manage your social media accounts and other software tools is equally important as protecting your accounts. One of the best ways to ensure hardware security is to install an antivirus solution.
It’ll prevent viruses and malware created by hackers from damaging your sensitive information and getting access to your accounts. An antivirus solution will scan your devices in real-time to protect them from cyberattacks and you won’t need to worry about doing it manually.
Another way to secure your hardware is to block access to certain websites. It includes sketchy and suspicious sites, known to have malware and viruses on them.
8. Keep Everything Updated
One thing that all hackers are always looking for is security loopholes within a system, which allows them to worm their way through. To combat this, software companies regularly update their solutions.
Therefore, you must keep all software solutions that your team uses up-to-date. It includes all the devices that your employees use, such as computers, smartphones, and tablets.
9. Inspect Your Inboxes Regularly
You should get into the habit of inspecting your social media inboxes regularly for suspicious activities. Make sure that you read all the emails from your social media regularly to monitor your accounts. You should also keep track of all the activities that your teams are performing.
Don’t forget to check the accounts you have signed up for but aren’t using at the moment. It’ll allow you to determine if there are any login attempts or unknown posts shared through your account. If you observe such an activity, make sure that you open your social media account and change its password.
Recommended for further reading
What to Do if Your Social Accounts Are Compromised
If your social media accounts do end up compromised for whatever reason, here’s the steps you should take.
Step 1: Prevent further damage
If you can still access your accounts:
Go into your account and update your password to a new, secure password. Reduce the number of employees with access to that password while you go on damage control. If you haven’t already, enable 2FA and make sure that no one has access to your secondary authentication method.
If you can’t access your accounts:
Create new accounts and report the hacked brand accounts. Get in touch with your social media’s support and try to recover your account. You may need to offer some identifying information to appropriately recover your accounts.
In both cases, stop publishing on your socials. If you use a social media management platform that does so, put a hard stop on any posts that are scheduled to publish. You need the space to control your brand accounts – so business-as-usual publishing needs to be paused while you get things under control.
Step 2: Be transparent with your audience and customers
If your accounts are compromised, you have an obligation to protect your audience and customers from any nefarious plans the hacker might have.
It’s important to release a statement saying:
- What happened to your social accounts
- How your accounts were compromised
- What danger is posed to your customers
- How you’re helping affected customers
- What steps you’re taking to prevent it from happening again in the future
Transparency will save you here. You’ll need to be honest about what happened to protect the trust your customers and audience have in you.
Step 3: Review Your Social Policy
Once the dust is settled and the fires are out, it’s time to take a hard look at your social media policy.
You’ll need to review the following aspects of that policy:
- Who has access to social accounts
- What security measures are in place
- How passwords are managed
- How to prevent further breaches
- What to do if a social account is breached in the future
The best defense is preventative. By reviewing your social policy, you’ll be able to better control what goes out on the biggest tool in your brand arsenal.
Final Words
Hackers who try to hack your social media account or mimic your brand to perform fraudulent activities can lead to reputation damage, stolen customer data, and revenue losses.
That’s why it’s important to know what tactics cybercriminals use for hacking and how you can protect your social media account for business from them.
At the end of the day, the best thing you can do to keep your social media accounts safe is to control how your passwords are managed, and use a social media management platform that prioritizes security.
Not all social media management platforms put the same importance on security and compliance – so when choosing your next social tool, look for one that’s specifically made with B2B social marketing in mind.